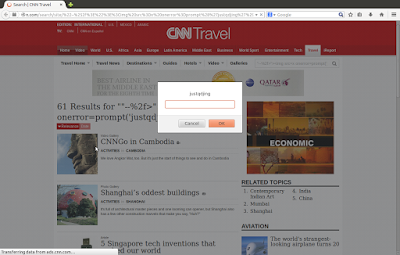
All Links in Two Topics of Indiatimes (indiatimes.com) Are Vulnerable to XSS (Cross Site Scripting) Attacks
(1) Domain Description:
http://www.indiatimes.com
"The Times of India (TOI) is an Indian English-language daily newspaper. It is the third-largest newspaper in India by circulation and largest selling English-language daily in the world according to Audit Bureau of Circulations (India). According to the Indian Readership Survey (IRS) 2012, the Times of India is the most widely read English newspaper in India with a readership of 7.643 million. This ranks the Times of India as the top English daily in India by readership. It is owned and published by Bennett, Coleman & Co. Ltd. which is owned by the Sahu Jain family. In the Brand Trust Report 2012, Times of India was ranked 88th among India's most trusted brands and subsequently, according to the Brand Trust Report 2013, Times of India was ranked 100th among India's most trusted brands. In 2014 however, Times of India was ranked 174th among India's most trusted brands according to the Brand Trust Report 2014, a study conducted by Trust Research Advisory." (en.Wikipedia.org)
(2) Vulnerability description:
The web application indiatimes.com online website has a security problem. Hacker can exploit it by XSS bugs.
The code flaw occurs at Indiatimes's URL links. Indiatimes only filter part of the filenames in its website. All URLs under Indiatimes's "photogallery" and "top-llists" topics are affected.
Indiatimes uses part of the links under "photogallery" and "top-llists" topics to construct its website content without any checking of those links at all. This mistake is very popular in nowaday websites. Developer is not security expert.
The vulnerability can be attacked without user login. Tests were performed on Mozilla Firefox (26.0) in Ubuntu (12.04) and Microsoft IE (9.0.15) in Windows 7.
POC Codes:
http://www.indiatimes.com/
http://www.indiatimes.com/top-
http://www.indiatimes.com/
http://www.indiatimes.com/top-
POC Video:
Blog Details:
http://securityrelated.blogspot.com/2014/11/two-topics-of-indiatimes-indiatimescom.htmlWhat is XSS?
"Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted web sites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user within the output it generates without validating or encoding it." (OWASP)
(3) Vulnerability Disclosure:
The vulnerabilities were reported to Indiatimes in early September, 2014. However they are still unpatched.
Discovered and Reported by:
Wang Jing, Division of Mathematical Sciences (MAS), School of Physical and Mathematical Sciences (SPMS), Nanyang Technological University (NTU), Singapore. (@justqdjing)
Related Articles:
http://seclists.org/fulldisclosure/2014/Nov/91
http://lists.openwall.net/full-disclosure/2014/11/27/6
http://permalink.gmane.org/gmane.comp.security.fulldisclosure/1256
https://progressive-comp.com/?l=full-disclosure&m=141705615327961&w=1
http://tetraph.blog.163.com/blog/static/234603051201501352218524/http://seclists.org/fulldisclosure/2014/Nov/91
http://lists.openwall.net/full-disclosure/2014/11/27/6
http://permalink.gmane.org/gmane.comp.security.fulldisclosure/1256
https://progressive-comp.com/?l=full-disclosure&m=141705615327961&w=1
http://www.techworm.net/2014/12/times-india-website-vulnerable-xss
https://cxsecurity.com/issue/WLB-2014120004
https://vulnerabilitypost.wordpress.com/2014/12/04/indiatimes-xss
http://diebiyi.com/articles/security/all-links-in-two-topics-of-indiatimes
http://www.inzeed.com/kaleidoscope/computer-security/all-links-in-two-topics-of-indiatimes
http://itsecurity.lofter.com/post/1cfbf9e7_54fc6c9
http://computerobsess.blogspot.com/2014/12/all-links-in-two-topics-of-indiatimes.html
http://whitehatview.tumblr.com/post/104310651681/times-of-india-website-vulnerable-to
http://www.tetraph.com/blog/computer-security/all-links-in-two-topics-of-indiatimes
http://www.tetraph.com/blog/computer-security/all-links-in-two-topics-of-indiatimes